Ransomware demands and payments declined in 2024, thanks to a combination of better law enforcement and defenses by companies, according to BakerHostetler’s annual Data Security Incident Response Report.
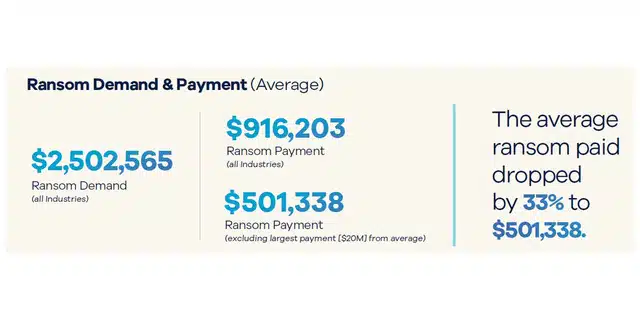
The average ransomware payment totaled $501,338 in 2024, excluding the largest payment, a 33% decline from the previous year. The amount of money demanded in a ransomware attack also declined, averaging just over $2 million, excluding the two largest known demands, down 24% from a year earlier.
The largest ransomware demand in 2024 was for more than $40 million and the largest payment was more than $20 million, according to the report.
BakerHostetler used insights and statistics drawn from guiding its clients through more than 1,250 data-security incidents in 2024 to compile the report. A Cleveland-based law firm, BakerHostetler specializes in digital assets, data management, and intellectual property.
A key factor in lowering ransomware demands and payments was law enforcement’s seizure and dismantling of LockBit’s infrastructure. LockBit is a cybercriminal group that offers ransomware-as-a-service technology. It has ranked among the top five ransomware organizations the past four years. The disruption of LockBit’s business led to disruption in the ransomware market, which resulted in disputes among ransomware “developers and affiliates” that created openings for smaller players “to accept lesser payments as they built their business” the report says.
Another factor in the decline of ransomware demands and payments is that many companies now have defenses in place to lessen the blow from an attack. “After years of attacks, the methods to prevent an attack and to recover effectively from an attack are more widely known,” Craig Hoffman, a BakerHostetler partner and co-leader of the firm’s Digital Risk Advisory and Cybersecurity team, says by email. “More companies have resilient backup capabilities, so fewer companies need to pay for a decryptor, a payment that is generally more expensive than only paying to prevent stolen data from being published.”
A decryptor unlocks files that have been encrypted in ransomware attacks.
In addition to the decrease in ransomware demands and payments, the costs of forensic investigations into cyberattacks dropped 30%, marking a three-year low. Since 2023, the average forensic investigation costs for the 20 largest network intrusions has declined to $273,000, down from $550,000. The median time to investigate an attack was 26 days. The median time to discover an attack was three days.
The decrease in forensic-investigation costs is largely attributable to companies becoming more proficient at investigating attacks. “It boils down to companies being better prepared to support investigations and forensic firms becoming more efficient,” Hoffman says.
One piece of bad news to emerge from the report is that wire fraud totaled $109 million in 2024, up from $35 million a year earlier, a threefold increase. The average fraudulent wire transfer was over $1 million. While the root causes for the increase have not been pinpointed, one factor is that criminals continue to improve their tactics, says Hoffman.
The report also reveals that the use of malware is decreasing. Instead, criminals are using compromised credentials to steal data. Malware is any software program designed to harm computer systems, steal data, or disrupt operations. Fueling the increased use of compromised credentials is that assets are accessible in the cloud and remotely. “So gaining access [to those assets] means you only need to be able to authenticate,” says Hoffman.
Hoffman adds that while companies have worked hard to protect their databases and to prevent installation of unauthorized programs, those defenses are essentially toothless when compromised credentials are used to gain entry. “If you authenticate as a legitimate user with stolen credentials, you need little or no malware to complete your goal,” Hoffman says.







